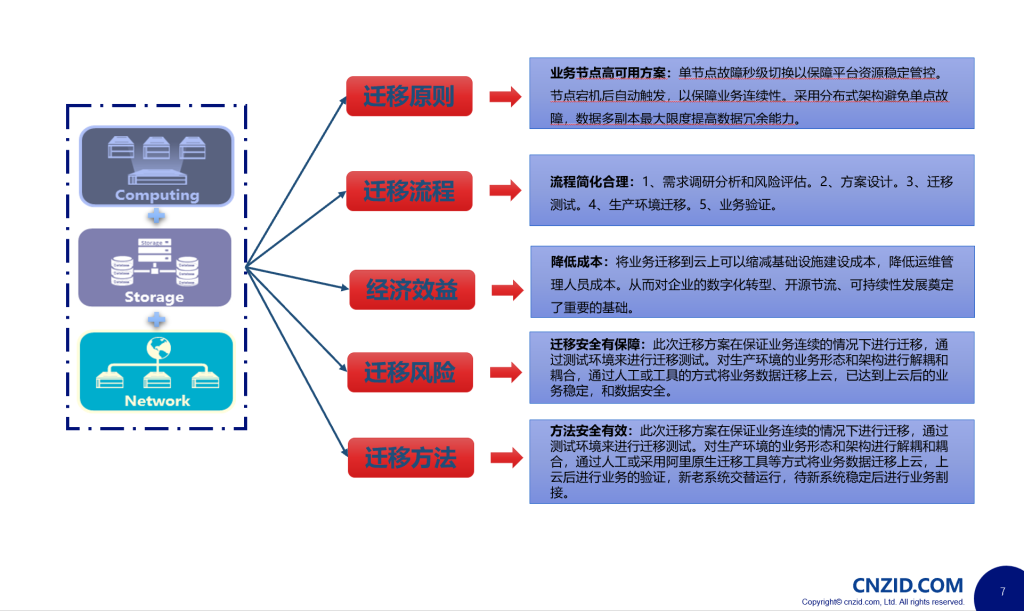
1、操作系统:centos7.9+bind9+mariadb+namedmanager-v1.9.o
2、修改yum源
cd /etc/yum.repos.d/
vim jethrocarr-c7-public.repo
# CentOS / RHEL 7 Repositories
#
# www.jethrocarr.com
#
# Packages of third party software that extend the OS and won't replace any
# standard OS or EPEL packages. Generally these are always safe to install
# since they won't override anything else that is present on a system if you're
# only using stock repos.
#
# Some of these packages may require packages in jethrocarr-updates.
[jethrocarr-os]
name=jethrocarr-os
baseurl=https://repos.jethrocarr.com/pub/jethrocarr/linux/centos/7/jethrocarr-os/$basearch/
gpgcheck=1
gpgkey=https://repos.jethrocarr.com/jethrocarr_signing_key.gpg
enabled=1
# Provides upgrades to packages included in the distribution (eg: PHP or the
# kernel). These packages could potentially break other applications you have
# installed onto your computer. Some of these packages may require packages
# in jethrocarr-os.
[jethrocarr-updates]
name=jethrocarr-updates
baseurl=https://repos.jethrocarr.com/pub/jethrocarr/linux/centos/7/jethrocarr-updates/$basearch/
gpgcheck=1
gpgkey=https://repos.jethrocarr.com/jethrocarr_signing_key.gpg
enabled=1
# All RPMs developed by Jethro Carr are located in this repository. Some of
# these programs may require packages in jethrocarr-os or jethrocarr-updates
# in order to install and run
[jethrocarr-custom]
name=jethrocarr-custom
baseurl=https://repos.jethrocarr.com/pub/jethrocarr/linux/centos/7/jethrocarr-custom/$basearch/
gpgcheck=1
gpgkey=https://repos.jethrocarr.com/jethrocarr_signing_key.gpg
enabled=1
3、安装软件包
yum install -y namedmanager-www namedmanager-bind bind-chroot
4、修改配置文件named.conf
vim /etc/named.conf
******************************************************************************************************
//
// named.conf
//
// Provided by Red Hat bind package to configure the ISC BIND named(8) DNS
// server as a caching only nameserver (as a localhost DNS resolver only).
//
// See /usr/share/doc/bind*/sample/ for example named configuration files.
//
// See the BIND Administrator's Reference Manual (ARM) for details about the
// configuration located in /usr/share/doc/bind-{version}/Bv9ARM.html
options {
listen-on port 53 { any; };
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
recursing-file "/var/named/data/named.recursing";
secroots-file "/var/named/data/named.secroots";
allow-query { any; };
/*
- If you are building an AUTHORITATIVE DNS server, do NOT enable recursion.
- If you are building a RECURSIVE (caching) DNS server, you need to enable
recursion.
- If your recursive DNS server has a public IP address, you MUST enable access
control to limit queries to your legitimate users. Failing to do so will
cause your server to become part of large scale DNS amplification
attacks. Implementing BCP38 within your network would greatly
reduce such attack surface
*/
recursion yes;
dnssec-enable yes;
dnssec-validation yes;
/* Path to ISC DLV key */
bindkeys-file "/etc/named.root.key";
managed-keys-directory "/var/named/dynamic";
pid-file "/run/named/named.pid";
session-keyfile "/run/named/session.key";
};
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
zone "." IN {
type hint;
file "named.ca";
};
include "/etc/named.rfc1912.zones";
include "/etc/named.root.key";
include "/etc/named.namedmanager.conf";
*********************************************************************
chown named.root /etc/named.namedmanager.conf
chkconfig --level 35 namedmanager_logpush on
5、配置数据库
systemctl start mariadb
mysqladmin -u root password 123456
/usr/share/namedmanager/resources/autoinstall.pl
6、修改config-bind.php配置文件
vim /etc/namedmanager/config-bind.php
******************************************************************************************************
<?php
/*
Sample Configuration File
Copy this file to config-settings.php
This file should be read-only to the user whom the bind configuration scripts are running as.
*/
/*
API Configuration
*/
$config["api_url"] = "http://192.168.5.137/namedmanager"; // Application Install Location
$config["api_server_name"] = "dns.myd.com"; // Name of the DNS server (important: part of the authentication process)
$config["api_auth_key"] = "dns"; // API authentication key
/*
Log file to find messages from Named. Note that:
* File should be in syslog format
* Named Manager uses tail -f to read it, this can break with logrotate - make sure that either "copytruncate" mode is used, or tail processes are killed
*/
$config["log_file"] = "/var/log/messages";
/*
Lock File
Used to prevent clashes when multiple instances are accidently run.
*/
$config["lock_file"] = "/var/lock/namedmanager_lock";
/*
Bind Configuration Files
Theses files define what files that NamedManager will write to. By design, NamedManager does
not write directly into the master named configuration file, but instead into a seporate file
that gets included - which allows custom configuration and zones to be easily added without
worries of them being over written by NamedManager.
*/
$config["bind"]["version"] = "9"; // version of bind (currently only 9 is supported, although others may work)
$config["bind"]["reload"] = "/usr/sbin/rndc reload"; // command to reload bind config & zonefiles
$config["bind"]["config"] = "/etc/named.namedmanager.conf"; // configuration file to write bind config too
$config["bind"]["zonefiledir"] = "/var/named/"; // directory to write zonefiles too
// note: if using chroot bind, will often be /var/named/chroot/var/named/
$config["bind"]["verify_zone"] = "/usr/sbin/named-checkzone"; // Used to verify each generated zonefile as OK
$config["bind"]["verify_config"] = "/usr/sbin/named-checkconf"; // Used to verify generated NamedManager configuration
/*
Unusual Compatibility Options
*/
// Include a full path to the zonefiles in Bind - useful if Bind lacks a
// directory configuration or you really, really to store you zonefiles
// in a different location
//
// $config["bind"]["zonefullpath"] = "on";
// force debugging on for all users + scripts
// (note: debugging can be enabled on a per-user basis by an admin via the web interface)
//$_SESSION["user"]["debug"] = "on";
?>
****************************************************************************
7、启动服务
systemctl start named
systemctl start httpd
hostnamectl set-hostname dns.myd.com
8、修改配置php.ini
将php.ini文件中的error_reporting = E_ALL改写成error_reporting = E_ALL & ~E_NOTICE(该方法关闭了PHP的提示功能)
9、修改apache配置
# vi /etc/httpd/conf/httpd.conf
# 这里将 ServerName 改为 192.168.65.123(修改成自己主机的IP地址或者域名)
ServerName 192.168.65.123
<Directory />
AllowOverride none
# Require all denied
</Directory>
# vi /etc/httpd/conf.d/namedmanager.conf
Alias /namedmanager /usr/share/namedmanager/htdocs
<Location /namedmanager>
Order allow,deny
Allow from all
AllowOverride None
Require all granted
</Location>
10、登录界面配置DNS服务器
web登录http://192.168.65.123/namedmanager/ 默认账号密码setup/setup123